Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
How AI Is Challenging Cybersecurity Efforts
5 Reasons Why NIS2 Directive Preparation Should Start Now, Part Two: Implementation Takes Time
In a previous blog post, I discussed the two main areas to audit before the European Union’s updated Network and Information Security Directive (NIS2) becomes ratified law in October 2024. Specifically, these audits would: Identify your gaps with the NIS2 directive’s requirements now. Review your current supply chain security flaws. Now that we’ve discovered these security flaws, we must fix them — before time runs out in October 2024.
Your Guide to ACSC Essential 8 Compliance
What are the Benefits of Using Cribl Stream with Amazon Security Lake?
In a recent user group meeting, guest speaker Marc Luescher from Amazon Web Services (AWS) joined us to give an overview of Amazon Security Lake. We talked about Cribl use cases and how Cribl Stream can bring your non-AWS data into the Security Lake. Enterprises are dealing with some significant challenges with security data in 2023. Inconsistent, incomplete, poorly-formatted log data is simultaneously scattered across companies and locked up in different silos within the organization.
5 Reasons Why NIS2 Directive Preparation Should Start Now, Part One: Audits Take Time
You probably heard about the European Union’s updated Network and Information Security Directive (NIS2). This directive will translate into active law in October 2024. You should be ready for it, as there are high fines and sanctions for non-compliance. But you might be tempted to think that October 2024 is far away, right? Think twice. After all, how can you know if you have plenty of time to prepare if you don’t know how well you currently comply with the projected regulations?
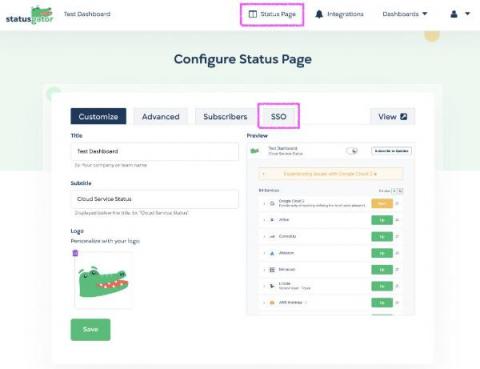
New Feature: Enhance Security with Status Page SSO
We’ve heard your feedback and it’s here: Status page SSO is now available on our Enterprise plan. Status Page Single Sign-On (SSO) empowers StatusGator customers to safeguard their status pages through a seamless Single Sign-On experience. You can now restrict access to your status page to only your team, employees, or users who have SSO access through your organization’s identity provider.
Blackhat 2023 Recap: How Will Advanced AI Impact Cybersecurity?
Online Security For Businesses: Threats, Weaknesses, And Solutions
How to Utilize Dark Web Monitoring Protection
Odds are, you've heard about the dark web. Nevertheless, you may be unsure about its threat to your business and how to address it. The dark web is a set of anonymously hosted websites within the deep web accessible through anonymizing software, commonly "TOR" (The Onion Router). The anonymity these websites provide makes them the perfect online marketplace for illegal activities.