Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Why You Need Security Operations
Build a resilient cybersecurity framework by transforming your IT team into a security team
More organizations than ever before have shifted to a hybrid work culture to reduce the impact of COVID-19. This unprecedented change has not only given rise to new security challenges, but has also considerably increased the surface area available for an attack. A blend of personal and corporate endpoints in use, geographical spread of resources, and a sharp spike in the overall number of security threats have further complicated the already labor-intensive security landscape.
Five worthy reads: Every month should be Cybersecurity Awareness Month!
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. Organizations on a global scale observe Cybersecurity Awareness Month to educate and instruct their employees on cybersecurity best practices. This week we highlight some cybersecurity trends that are shaping the industry today.
Security misconfiguration prevention | ManageEngine Vulnerability Manager Plus
How to Keep Your Digital Devices Current
Pop quiz: An employee just submitted a ticket to IT about recurring application crashes. When IT finally gets back to them, what is the first thing they ask? Answer: “When did you last update your device?” If this rings true, there is a reason. Outdated devices and applications can quickly detract from digital employee experience and IT notoriously struggles to detect and resolve these issues at scale.
Detecting Google Cloud Platform OAuth Token Abuse Using Splunk
In a recent post by the Splunk Threat Research team, we addressed permanent and temporary token/credential abuse in AWS and how to mitigate credential exposure. With 94% of Enterprises using a cloud service, and some using at least five different cloud platforms, it’s imperative to stay ahead of threats across multicloud environments. Let’s now turn our attention to Google Cloud Platform (GCP) and how to detect and mitigate OAuth Token Abuse.
Securing Your Monitoring Infrastructure
Your monitoring system provides a comprehensive overview of any infrastructure. To effectively monitor your infrastructure and systems, you’ll need to get all of your data into one place - regardless if you have 1 node or 10 nodes. This centralization of data inevitably creates a vulnerable point that attackers can potentially target and exploit. In this article, we look at how to design your infrastructure in a secure way, as well as focus in on how to secure your nodes.
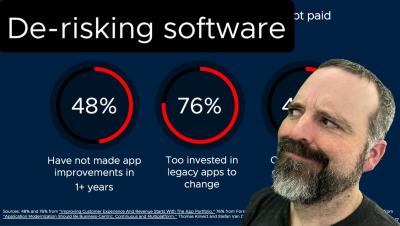
Tanzu Talk: De-risking software
How to automate VPC Mirroring for Coralogix STA
After installing the Coralogix Security Traffic Analyzer (STA) and choosing a mirroring strategy suitable for your organization needs (if not, you can start by reading this) the next step would be to set the mirroring configuration in AWS.