Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
How to monitor Kubelet
Monitor Kubelet is key when running Kubernetes in production. Kubelet is a very important service inside Kubernetes’ control plane. It’s the component that cares that the containers described by pods are running in the nodes. Kubelet works in a declarative way by receiving PodSpecs and ensuring that the current state matches desired pods.
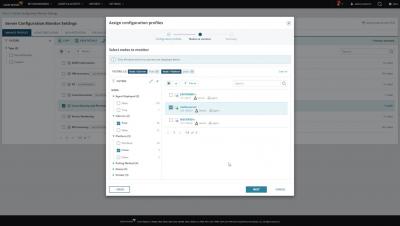
How to Monitor User Permissions on Linux Servers With SolarWinds Server Configuration Monitor
Guide: Smarter AWS Traffic Mirroring for Stronger Cloud Security
So, you’ve installed Coralogix’s STA and you would like to start analyzing your traffic and getting valuable insights but you’re not sure that you’re mirroring enough traffic or wondering if you might be mirroring too much data and could be getting more for less. The harsh truth is that in order to be able to detect everything, you have to capture everything and in order to be able to investigate security issues thoroughly, you need to capture every network packet.
What Is IT Risk Management? A Leader's Introductory Guide
Do you own or manage a business? Managing a company involves many steps. These steps begin right from the genesis of an idea through its execution. They also involve choosing a development procedure and managing risks. Most software companies these days are adopting the latest project methodologies, like DevOps and agile.
IT security: Disrupting the cybersecurity kill chain by detecting domain reconnaissance
Cyberattacks are a growing threat, and organizations are investing time and money in security strategies to make certain that their infrastructures are secure. Active Directory (AD) is a constant target for compromise, as it’s at the core of any organization’s security — it handles authentication and authorization for all users in an organization.
SOCtails Episode 3 - The Cybersecurity Olympics
Five worthy reads: Mastering cybersecurity with AI and machine learning
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we discuss the escalating significance of AI and machine learning in IT security space.
SOAR In Your Pocket
Hi, Let's take a look behind the scenes and find out how Security Orchestration Automation and Response (SOAR) solutions can have a positive impact on your security investigation and response efficiency. In this article, I'll also highlight how Phantom-mobile makes your life as the “officer on duty” a lot easier.
How to troubleshoot Kubernetes OOM and CPU Throttle
Experience Kubernetes OOM kills can be very frustrating. Why is my application struggling if I have plenty of CPU in the node? Managing Kubernetes pod resources can be a challenge. Many issues can arise, possibly due to an incorrect configuration of Kubernetes limits and requests. In this article, we will try to help you detect the most common issues related to the usage of resources.