Transforming Compliance and Operational Efficiency: A Success Story with Motadata AIOps APIs
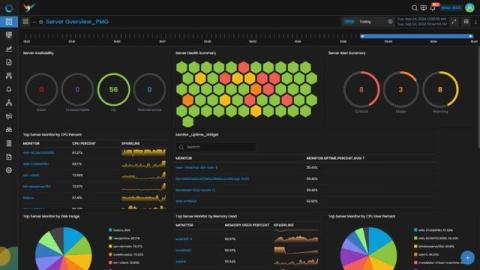
In the fast-paced world of equity broking, compliance with regulatory requirements and operational efficiency are paramount. Broking platforms must ensure that their systems are not only continuously monitored, but their data is accurately reported to regulatory bodies. This is a story of how a leading equity broker from India leveraged our AIOps APIs to meet their regulatory compliance requirements while achieving operational excellence.