How to query private network data without an agent using AWS and Grafana Cloud
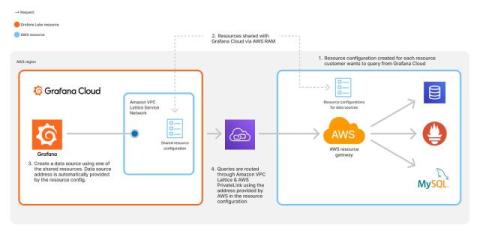
Connecting to data sources in a private network or an Amazon Virtual Private Cloud (Amazon VPC) can require extra attention to the network security configuration to prevent unintended network exposure. For example, if you wanted to query a network-secured data source, like a MySQL database or an Elasticsearch cluster, that is hosted in an on-premises private network, you would need to open your network to inbound queries from a range of IP addresses.