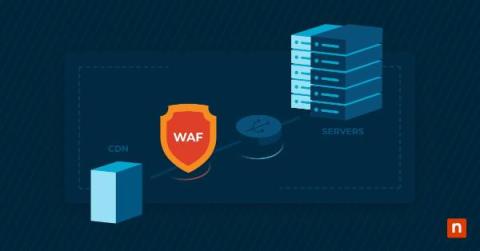
Discover 7 New Major Features on Qovery
I'm thrilled to unveil a suite of groundbreaking features that we've introduced over the past four months at Qovery. Our commitment to enhancing your development and deployment experience continues to be our driving force. Recently, we shared these updates during our exhilarating public demo day, which you can watch here. Let's dive into the features that are set to redefine your interaction with Qovery.