Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Let's go phishing! Email security trends to keep up with in 2022
Although it’s good to stay optimistic for 2022, it’s difficult to deny that the main challenges the world has been facing since the beginning of the pandemic are still among us. Cybersecurity continues to be one of the key global targets for criminals in a world where an ever-increasing percentage of the workforce is shifting to working from home (WFH), leaving organizations more vulnerable than ever to a wide array of threats.
Minimize the Risk of Logging Over the Internet: How LogStream Cloud Can Be Paired With Cloudflare
With the proliferation of security SaaS platforms, such as Cloudflare, Proofpoint, and PingOne, enterprises must figure out how to integrate third-party data shipped over the internet into their analytics and SIEM platforms. This requirement to integrate third-party data raises a host of security, infrastructure, and data quality questions. Enterprises can lower risk, and complete projects faster, by using Cribl LogStream Cloud to solve their challenges in managing third-party SaaS platform data.
CVE-2021-44521 - Exploiting Apache Cassandra User-Defined Functions for Remote Code Execution
Puppet Enterprise installation and self-signed Intermediate CA
This article is about how to install Puppet Enterprise using your own self-signed Intermediate CA (Certificate Authority). In some environments, regulations require you to intercept and inspect all SSL traffic to detect malicious activities that could otherwise masquerade as legitimate encrypted traffic. This requires the ability to decrypt and re-encrypt the stream in real time, which can only be done with the proper certificates installed.
Writing a cfbs module for your custom policy update
I re-stumbled across this mailing list post from Bryan Burke about some policy framework upgrade issues where he also asked about hooking in and customizing the update policy. I thought this sounded like a good opportunity for an example using a cfbs module. So, let’s take a look at making a cfbs module for a custom update policy. As mentioned in the thread there are just a couple of things you need to do in order to hook in and customize the behavior of the update policy.
DDOS Attacks: How to Protect Yourself from the Political Cyber Attack
In the past 24 hours, funding website GiveSendGo has reported that they’ve been the victim of a DDOS attack, in response to the politically charged debate about funding for vaccine skeptics. The GiveSendGo DDOS is the latest in a long line of political cyberattacks that have relied on the DDOS mechanism as a form of political activism. There were millions of these attacks in 2021 alone.
Why you need Tigera's new active cloud-native application security
First-generation security solutions for cloud-native applications have been failing because they apply a legacy mindset where the focus is on vulnerability scanning instead of a holistic approach to threat detection, threat prevention, and remediation. Given that the attack surface of modern applications is much larger than in traditional apps, security teams are struggling to keep up and we’ve seen a spike in breaches.
Webinar Recap: Force Multiply Your Security Operations Teams with Cribl LogStream
We hosted a webinar a few weeks back on using Cribl LogStream to make your security operations more scalable, efficient, and cost-effective. The turnout was fantastic and, while we answered most of the audience’s questions live, we couldn’t get to all of them. So I’ll go through the questions we couldn’t get to and offer some answers. Along the way, I’ll also share the results of two polling questions we asked during the webinar.
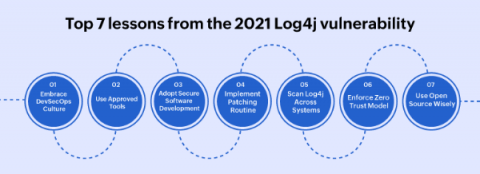
Top 7 lessons from the 2021 Log4j vulnerability
The Log4Shell (CVE-2021-44228) zero day vulnerability in the Java logging framework Log4j (versions 2.0 to 2.14.1) was revealed on December 9, 2021. The Apache Foundation assigned the maximum CVSS score of 10 to Log4Shell, as millions of servers and potentially, billions of devices came under risk. Security professionals around the world began patching the vulnerability, and scanning their systems to rule out any potential breach.