Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
What is a Supply Chain Attack (and What Can You Do About It)?
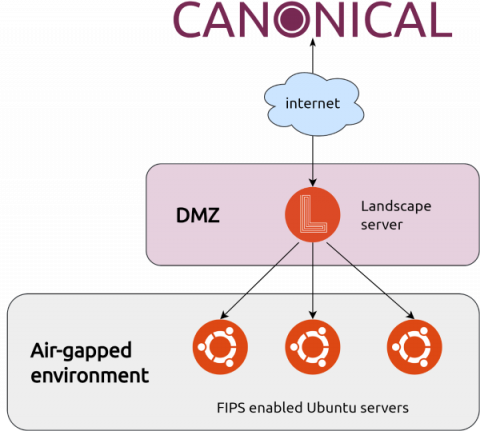
Enabling Ubuntu FIPS 140 in air-gapped environments
Many US military, government or critical national infrastructure organisation workloads that require FIPS compliance are also required to be deployed in air-gapped environments to provide an extra layer of protection.
Create and Manage Registry Secrets with VMware Tanzu Mission Control
Operators using VMware Tanzu Mission Control can now create and manage image registry secrets. This new feature of Tanzu Mission Control enables people to create image registry secrets in a single namespace and make them available for use by all namespaces in a cluster, providing a single place to manage all registry secrets for that cluster.
Five Ways To Reduce Your Cloud Security Blast Radius
It takes only a glance at the daily headlines to see that cybercriminals are using increasingly sophisticated methods to breach cloud defenses and access sensitive data. The complexity of cloud frameworks makes it extraordinarily difficult to detect nefarious activities. In many cases, attackers lurk in systems for weeks or months before pulling the trigger.
Secure Your Software Supply Chain with New VMware Tanzu Application Platform Capabilities
VMware Tanzu Application Platform is a modular, application-aware platform that gives developers a prepaved path to production for building and deploying software on any compliant public cloud or on-premises Kubernetes cluster. Designed to deliver a superior and secure developer experience, it makes the software supply chain even more secure with a suite of features, including vulnerability scanning, a software bill of materials, and image signing, and more.
Introducing Datadog Application Security
Securing modern-day production systems is expensive and complex. Teams often need to implement extensive measures, such as secure coding practices, security testing, periodic vulnerability scans and penetration tests, and protections at the network edge. Even when organizations have the resources to deploy these solutions, they still struggle to keep pace with software teams, especially as they accelerate their release cycles and migrate to distributed systems and microservices.
Securing DNS: interrupting attacks as early as possible
While MSPs have been making significant investments in security and offering services, it is a challenge to keep up with the frequency and evolving sophistication of today’s cybersecurity threats. Defense in Depth (DiD) is the foundation on which most MSPs have built a layered security approach for dealing with them.
Optimized Security Traffic Mirroring Examples - Part 1
You have to capture everything to investigate security issues thoroughly, right? More often than not, data that at one time was labeled irrelevant and thrown away is found to be the missing piece of the puzzle when investigating a malicious attacker or the source of an information leak. So, you need to capture every network packet.
CFEngine bootstrap with Ansible
CFEngine and Ansible are two complementary infrastructure management tools. Findings from our analysis show that they can be combined and used side by side with joint forces to handle all areas in the best possible way. Part of infrastructure management is hosts deployment, either when building a brand new infrastructure or when growing one by adding new hosts.