Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
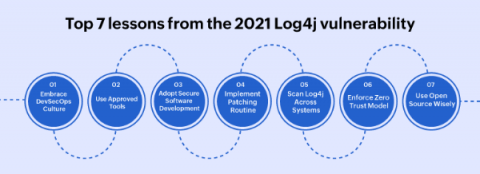
Top 7 lessons from the 2021 Log4j vulnerability
The Log4Shell (CVE-2021-44228) zero day vulnerability in the Java logging framework Log4j (versions 2.0 to 2.14.1) was revealed on December 9, 2021. The Apache Foundation assigned the maximum CVSS score of 10 to Log4Shell, as millions of servers and potentially, billions of devices came under risk. Security professionals around the world began patching the vulnerability, and scanning their systems to rule out any potential breach.
How to Test Multi-Factor Authentication for Microsoft Teams
Our last blog introduced Multi-Factor Authentication (MFA) for synthetics and discussed how MFA works. Most of our customers use Microsoft Teams as their Go-To messaging and collaboration application. So in today’s article I will show you how to deploy the Teams Audio Video sensor in your environment with an MFA configuration. This will enable testing MFA while at the same time testing the performance of a Teams audio video conference.
NinjaOne Hires Former Head of Security at Splunk, Guardant Health as Chief Trust Officer
Five Key Steps for Database Security in the Cloud Age
As business has become more digital, data has become the most valuable asset of many organizations. But protecting that data has also become much more complicated as organizations increasingly migrate it to a mix of public and private cloud infrastructures, such as Microsoft Azure, Amazon Web Services, and Google Cloud.
My pledge for Safer Internet Day
I was asked to write a pledge to help promote the importance of Safer Internet Day, which is taking place February 8. If you are not familiar with Safer Internet Day, it is a day dedicated to highlighting practical ways in which you can be involved in creating and maintaining a better online world. You can read more about it here. I took on this task and actually came up with two pledges: a personal and business one.
Open Source Cybersecurity: Towards a Democratized Framework
Today, anyone can contribute to some of the world’s most important software platforms and frameworks, such as Kubernetes, the Linux kernel or Python. They can do this because these platforms are open source, meaning they are collaboratively developed by global communities. What if we applied the same principles of democratization and free access to cybersecurity?
Chimera: Painless OAuth for Plugin Frameworks
Plugins can help teams unlock the full potential of Mattermost, but they aren’t always ready to go out of the box. Learn how Chimera streamlines plugin configuration via an OAuth2 Proxy. One of the best aspects of any software offered in the Cloud is the ability to start using it in just a matter of minutes. The same is true for the Mattermost Cloud offering.
Introducing bodies with custom promise types
Last year we had a look at managing local groups with the custom groups promise type. As you may or may not recall, we used JSON-strings to imitate CFEngine bodies. This was due to the fact that the promise module protocol did not support bodies at that time. Today, on the other hand, we’re happy to announce that as of CFEngine 3.20, this will no longer be the case. In this blog post we’ll introduce the long awaited feature; custom bodies.
The Observability Lake: Total Recall of an Organization's Observability and Security Data
Enterprises are dealing with a deluge of observability data for both IT and security. Worldwide, data is increasing at a 23% CAGR, per IDC. In 5 years, organizations will be dealing with nearly three times the amount of data they have today. There is a fundamental tension between enterprise budgets, growing significantly less than 23% a year, and the staggering growth of data.