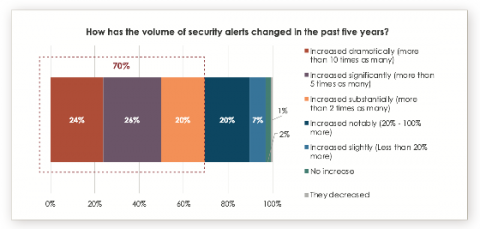
COVID-19's Impact On Infrastructure Security
It’s no secret that COVID-19 is negatively impacting businesses of all sizes in a number of ways. Some more obvious than others. Unless you are in IT, you’re probably not thinking of how COVID-19 can affect the infrastructure security of your organization, but the truth is that as businesses make the tough decision to layoff employees in order to stay in business, basic security hygiene can easily be overlooked.