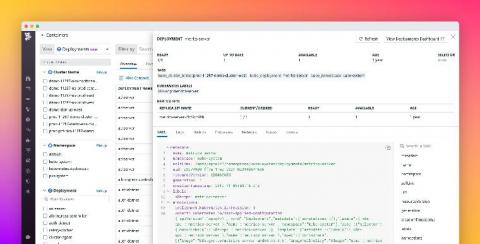
Is IT Prepared for a Hybrid Remote Workplace Environment?
Return to work is happening. After working remotely from home for months due to Covid, companies are now offering employees the option to return to their workplace. In a survey done by Google, 62% of its workers would like to return to the office at some point and see their work future as more flexible. This sentiment is catching up among the rest of the enterprises in Silicon Valley and the rest of America. The hybrid remote workplace model continues to be appreciated by employees seeking to spend more time with family and engaging with the office community.