NiCE Recording Monitoring NetApp on Microsoft SCOM 2024Q3
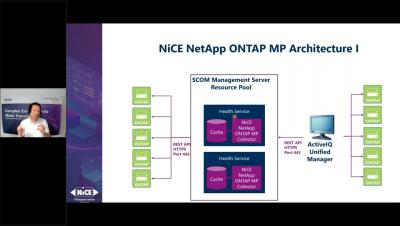
Keeping your storage systems performing at their best is essential for smooth business operations. That’s why it’s crucial to integrate NetApp into Microsoft System Center Operations Manager (SCOM) for a comprehensive monitoring solution. Many clients already use tools like Active IQ and System Manager, but the real magic happens when these tools work together seamlessly.