Securing IT in healthcare organizations: All you need to know
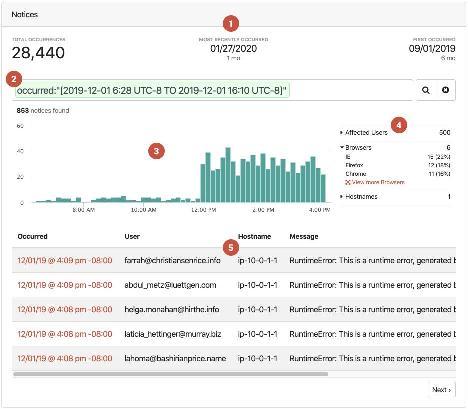
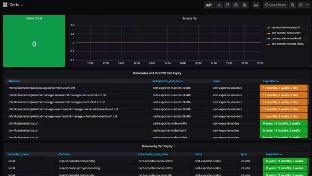
From maintaining electronic health records and generating medical reports, to carrying out robot-assisted surgeries and setting up online doctor-patient communication portals, the healthcare industry is becoming increasingly reliant on technology to effectively carry out day-to-day operations. While incorporating advanced technology assists healthcare professionals in providing better care for patients, it also increases the attack surface for cybercriminals looking to exploit sensitive data.