How to Build a Proactive Security Strategy Using Threat Intelligence
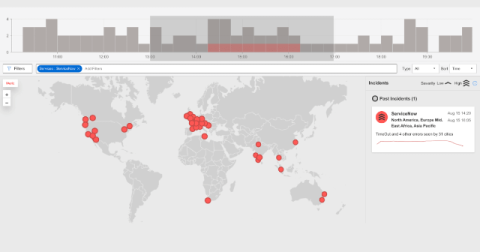
Proactive and reactive cybersecurity methods work hand in hand to shield your organization from various threat actors. Both protect your sensitive information from malicious parties. However, you must pay extra attention to your proactive security strategy. The devil you don't know is more dangerous than the devil you know. Concentrating on discovering unknown threats and stopping attacks before they happen can spare you from potentially eye-watering data breaches. To ensure your proactive cybersecurity strategy works like a charm, maximize threat intelligence.