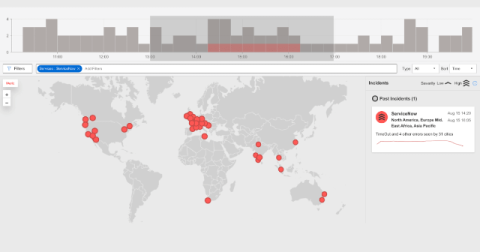
Learnings from ServiceNow's Proactive Response to a Network Breakdown
ServiceNow is undoubtedly one of the leading players in the fields of IT service management (ITSM), IT operations management (ITOM), and IT business management (ITBM). When they experience an outage or service interruption, it impacts thousands. The indirect and induced impacts have a multiplier effect on the larger IT ecosystem. Think about it. If a workflow is disrupted because of an outage, then there are large and wide ripple effects. For example: The list goes on.