Fantastic Cribl Packs and How to Export Them
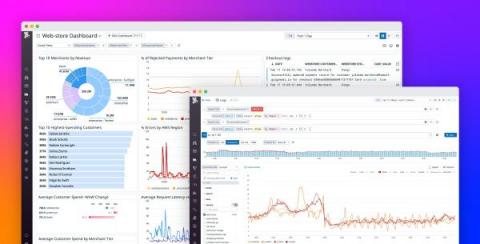
In LogStream 3.0, we introduced a framework that provides a way for LogStream customers to build, reuse, and share configuration modules – including pipelines, lookups, data samples, and knowledge objects – called Packs. While each Pack has its own “context” containing custom pipelines, routes, lookups, variables, etc., it still retains access to built-in LogStream configuration that is shipped with the product.