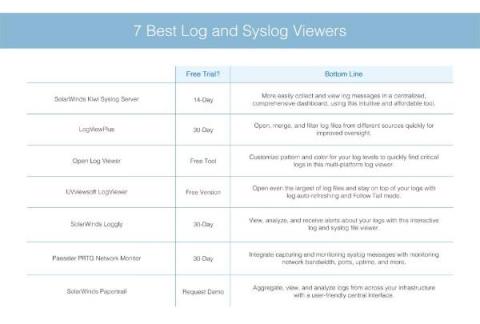
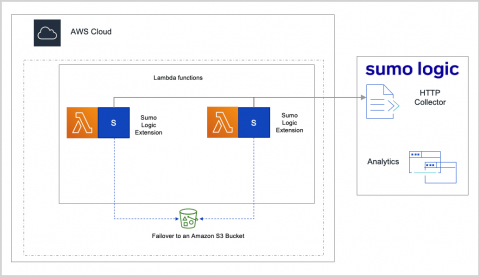
Application Logging in 2021
Have you ever written a Hello, World! application? In most of these tutorials the first step is to log words to the console. It's an easy way to understand what is going on with your application and readily available in every programming language. The console output is incredibly powerful, and it has become easier than ever to capture that output as logs. As your application grows and evolves you need to implement a structured application log approach.