Organizations, the ultimate way to manage your users and projects
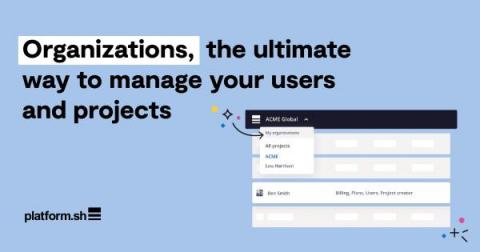
Organizations thrive on organization. But as the number of projects and contributors you organize within your organization grows, it becomes more and more difficult to organize your organizational permissions. That’s why we’ve introduced a new type of organizational layer that we’ve cleverly named Organizations. Organizations allow your key contributors to manage your projects and billing, thus removing the bottleneck on the legacy project owner.