Operations | Monitoring | ITSM | DevOps | Cloud
Monitoring
The latest News and Information on Monitoring for Websites, Applications, APIs, Infrastructure, and other technologies.
An Overview of Intelligent Query Processing in SQL Server
How to monitor your first Host with Icinga Director
Creating a new Host within the Icinga 2 configuration files is fairly easy. Basically you only have add an object of the type “Host” to a config file and reload Icinga 2. Doing the same with Icinga Director is even easier, you don’t even have to bother with terminal editors and configuration files. However, what sounds so easy for an experienced user may not be so obvious for beginners.
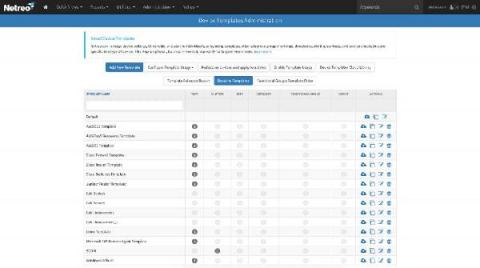
How To: Create Device Templates in Netreo
Automation is key to getting the most from the Netreo Platform. It is also a significant reason why Netreo delivers the fastest time-to-value among IT infrastructure management solutions. Automating administrative tasks reduces admin burden, improves data integrity and infrastructure lifecycle management . This allows you and your IT team t o focus on more strategic business initiatives.
New Google Cloud instance types on Elastic Cloud
We are excited to announce support for Google Compute Engine (GCE) N2 general purpose virtual machine (VM) types, and additional hardware configuration options powered by N2 custom machine types. N2 VMs leverage Intel 2nd Generation Xeon Scalable processors and provide a balance of compute, memory, and storage. N2 machine types also offer more than a 20% improvement in price-performance over the first-generation N1 machines.
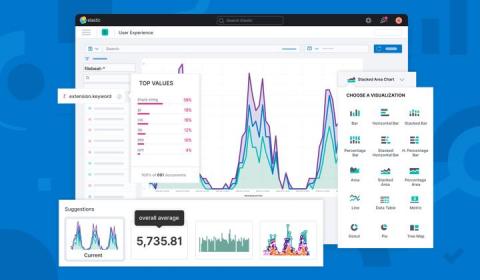
10 common questions answered with formulas and time travel in Kibana
Kibana creates easy ways to do powerful things with all of your data — to ask and answer questions and follow the flow of analysis. Many times the answer to your question requires calculations based on queried data. Formulas allow you to author your own metrics by combining multiple aggregated fields using math operations. In addition, moving through and replaying your data in time and space are powerful ways to gain historical context and understand additional insight about the present.
How to Test JavaScript Lambda Functions?
Function as a service (FaaS) offerings like AWS Lambda are a blessing for software development. They remove many of the issues that come with the setup and maintenance of backend infrastructure. With much of the upfront work taken out of the process, they also lower the barrier to start a new service and encourage modularization and encapsulation of software systems. Testing distributed systems and serverless cloud infrastructures.
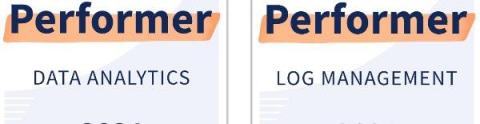
Logit.io named as a Performer in log management & data analytics award
We are excited to announce that Logit.io has recently taken home three awards from Appvizer’s selection ranking the best log management and data analytics tools on their platform. In addition to this, we’ve also been named as one of their certified partners for 2021.
Supercharge Storage Optimization Via Graylog
Just how smart is your storage management? Storage is one of the most promising ways to shift from the "more is better" philosophy to the "work smarter" philosophy. What do I mean by that? Historically, IT managers who needed more storage responded in the most obvious way: they bought more. Then they deployed it, integrated it, and waited until the problem recurred.
7 Ways To Amp Up Website Security Without Ditching Great UX Design
Technology has paved the way for businesses to reach out to more customers and clients. One of the most effective ways to reach more people is through the Internet, by creating a great website. Nowadays, businesses with websites have a name and face in the online world. However, as technology advances, so do security risks. If hackers get into a website, they can steal sensitive data – say, customer information (i.e., payment methods, addresses, etc.).