Investigating Network Anomalies - A sample workflow
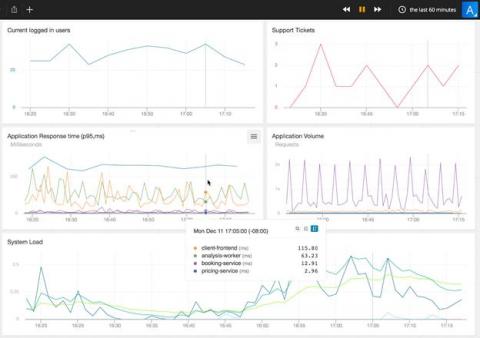
Network anomalies vary in nature. While some of them are easy to understand at first sight, there are anomalies that require investigation before a resolution can be made. The MITRE ATT&CK framework introduced in Kemp Flowmon ADS 11.3 streamlines the analysis process and gives security analyst additional insight by leveraging knowledge of adversaries' techniques explaining network anomalies via the ATT&CK framework point of view.