Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Why Torq's Momentum Mirrors the Exponential Adoption of No-Code Security Automation
In just three quarters since Torq was officially launched, our visionary team has delivered a 385% increase in customers, resulting in 360% quarter-over-quarter growth. We’ve also boosted our headcount by 150% and now have more than 100 technology integration partners, including Armis, Orca, SentinelOne, and Wiz. In addition, we recently opened new offices in the UK, Spain, and Taiwan
Zero Trust: The New Security Model for Cloud Native Applications and Infrastructure
Zero Trust security is gaining attention and momentum as a security approach or mindset that can improve the security posture of enterprises as they continue to battle hackers. Because of this widespread attention on Zero Trust, every software security vendor seems to be jumping on the Zero Trust bandwagon. However, Zero Trust is not a product or service. No single product or vendor can sell you Zero Trust security.
10 ways to make your software pipeline more observable
Ciara lists 10 ways to make your software pipelines more transparent and observable to gain insights, identify unusual behavior and possibly prevent a software supply chain attack.
SIEM-pler Migrations with Cribl Stream
A SIEM (Security Information Event Management) platform, along with several other tools that make you crave Alphabet Soup (XDR, UBA, NDR, etc), is a critical component of any organization’s security infrastructure. Between a constantly growing volume of logs, increasing attacks and breaches, and challenges finding qualified staff, many organizations may consider a SIEM migration. There could be several reasons for this.
How to Secure Your Data in the Cloud
We’ve entered a time when hard drives are becoming less important than data speeds, syncing, and remote storage. More and more end-users are saving their files in the cloud for convenience, safety, and cost savings. That said, some people still have concerns about cloud computing -- namely around security. How safe are files that are stored hundreds or thousands of miles away, on some other organization’s hardware?
ManageEngine Integrates with Sectigo® to Automate Certificate Lifecycle Management
Is Online Privacy Dead? Why Companies Infringe on Your Digital Rights
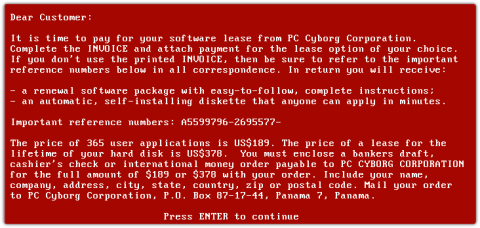
Battle the Ransomware Scourge with Deep Network Insight
Ransomware is the gift that keeps on giving. Old as it is (33 years) ransomware is constantly morphing into new exploits. The reason is simple. Ransomware works and too often cybercriminals walk away with bags of money (or piles of Bitcoin, anyway). “Following the World Health Organization's AIDS conference in 1989, Joseph L. Popp, a Harvard-educated biologist, mailed 20,000 floppy disks to event attendees.
The Internet's Mid-Life Crisis - Black Hat at 25
“Why is it so bad right now? Why does it seem like we’re fighting this up-hill battle?” The internet, it seems, is having a mid-life crisis. As industries progress through their life cycle, they are expected to reach a quasi-steady state of maturity, but the internet hasn’t gotten that message. In fact, it seems to be stuck in the growth phase, expanding exponentially with no end in sight, and securing it just feels so hard. Let’s dive into my Black Hat recap.