Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
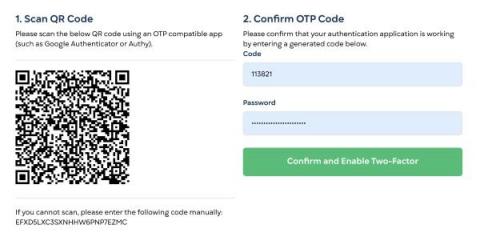
Protect your StatusGator Account with Two-Factor Auth
StatusGator now supports Two-Factor Authentication, often called 2FA, a more secure way of signing into your account. Using an authenticator app such Google Authenticator, Authy, or a password manager like 1Password, you can now protect your StatusGator account with a second authentication factor, a one-time password (OTP) that you enter after signing in.
Is Cybersecurity Hard? The Basics Made Easy To Understand
SOC 2 Compliance - What is it?
In today's world, information security is a noteworthy concern for all organisations, including those outsourcing vital enterprise operations to third parties. Enterprises are vulnerable to data theft, extortion, and malware installation when mishandled data, particularly by application and network security providers. American Institute of Certified Public Accountants (AICPA) was the organization that created SOC 2 which stands for ‘Service Organization Control 2'.
Are your applications secured end-to-end?
Kubernetes has grown immensely, and its use within organizations is maturing. While Kubernetes’ growth is exciting, security concerns around applications deployed on Kubernetes are mounting. Red Hat performed a survey with hundreds of DevOps professionals, and it showed that 55% delayed application releases due to security issues.
How to retrieve Azure Key Vault Secrets using Azure Functions (Part I)
How to Leverage Cribl and Exabeam: Parser Validating
Organizations leverage many different cybersecurity and observability tools for different departments. It’s common to see the IT department using Splunk Enterprise, while the SOC uses Exabeam. Both of these tools use separate agents, each feeding different data to their destinations. Normally this isn’t a problem unless you’re talking about domain controllers. Domain controllers only allow a single agent, meaning you can’t feed two platforms with data.
Key considerations before signing up for cyber insurance
With 2021 seeing 5.1 billion records breached and an annual increase in attacks at 11%, the risk of security incidents is only getting greater every year. And when an attack hits, the cost to recover, which includes fines, penalties, legal fees, and much more, are also great. To help minimize the scope of financial damage, many organizations turn to cyber insurance. Albeit a relatively new branch of insurance, demand is already huge and ever increasing.
How To Secure Your Business Digitally?
How Chatbot Automation Benefits Security Teams
When you hear the term “chatbot,” your mind may at first turn to things like robotic customer support services on retail websites – a relatively mundane use case for chatbots, and one that is probably hard to get excited about if you’re a security engineer. But, the fact is that chatbots can do much more than provide customer support.