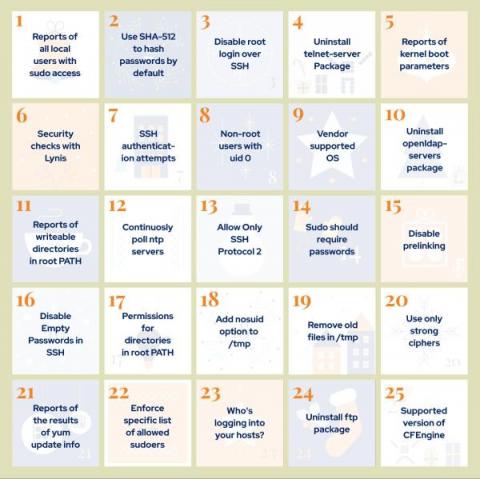
My New Year's Resolution: Going Passwordless!
What is your New Year’s resolution for 2022? Well, it is that time of year again! My resolutions are not necessarily new, but a continuation of several that I have made in prior years. Eat healthier foods, lose weight, and save money are the ones that immediately come to mind. Another best practice that I started several years ago was to adopt a passwordless authentication initiative for all my internet connected personal devices.