Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
How to Connect Elastic Security to Jira - Version 7.10
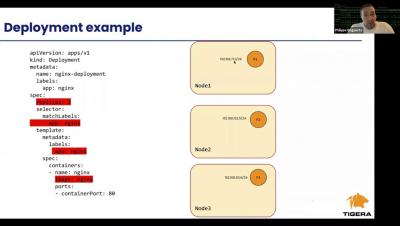
Understanding Kube-Proxy
Automation Made Easy: What's New with Splunk Phantom
The Splunk Security Team is excited to share some of the new and enhanced capabilities of Splunk Phantom, Splunk’s security orchestration, automation and response (SOAR) technology. Phantom’s latest update (v4.10) makes automation implementation, operation and scaling easier than ever for your security team.
How Clorox leverages Cloud SIEM across security operations, threat hunting, and IT Ops
Hacked! Solve the Dreaded DevOps Problem With This
Hacks that make headlines are painful for everyone involved, but with some clever preparation and web monitoring at your side you can avoid the worst of this pain. Those who have been victimized face a steep uphill battle to reclaim trust and authority. Unwitting victims, like customers and end users, suffer downtime or leaks containing personally identifiable information. If your eye is not on security, your organization is inviting these kinds of attacks.
How to Contribute to Detection Rules in Elastic Security - Version 7.10
Stop Enforcing Security Standards. Start Implementing Policies.
In days gone by, highly regulated industries like pharmaceuticals and finance were the biggest targets for nefarious cyber actors, due to the financial resources at banks and drug companies’ disposal – their respective security standards were indicative of this. Verizon reports in 2020 that, whilst banks and pharma companies account for 25% of major data breaches, big tech, and supply chain are increasingly at risk.
MSP Security Incident Response Planning (a Quick Guide)
Threat Thursdays: 2020 A Year in Review
We can finally bid a not so fond farewell to 2020. Looking back at our Threat Thursday series in reflection there is no way other than to say 2020 was a brutal year in cybersecurity. 2019 had already driven ransomware into high gear, but the seven-figure ransom extorted from Travelex really set the tone for what was to come this year. The New Year is a time to reflect, but most importantly it’s a time to learn from the past to create a safer, more secure future.