Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Datadog on Serverless
Elastic Security provides free and open protections for SUNBURST
On December 13, SolarWinds released a security advisory regarding a successful supply-chain attack on the Orion management platform. The attack affects Orion versions 2019.4 HF 5 through 2020.2.1, software products released between March and June of 2020. Likewise, on December 13, FireEye released information about a global campaign involving SolarWinds supply-chain compromise that affected some versions of Orion software.
3 Tips for MSPs to Handle Cyber Attacks
Logit.io Achieves PCI Service Provider Compliance
We’re happy to announce that we’ve successfully completed PCI (Payment Card Industry Data Security Standard) Service Provider Certification. This means that at Logit.io we are committed to the security of storing, processing and transmitting credit card transactions.
SUNBURST Backdoor: What to look for in your logs now - Interview with an incident responder
Yesterday, FireEye published a report about a global intrusion campaign that utilized a backdoor planted in SolarWinds Orion. Attackers gained access to the download servers of Orion. They managed to infect signed installers downloaded by Orion users who had all reason to believe that the packages are safe and had not been tampered with. With this information out in the world, teams are scrambling to investigate if their environments are affected by this breach.
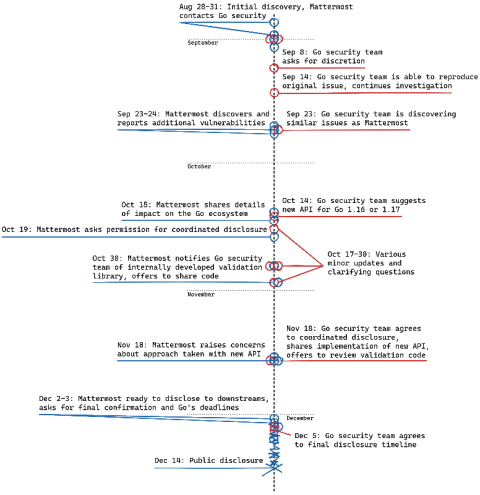
Coordinated disclosure of XML round-trip vulnerabilities in Go's standard library
This blog post is a part of Mattermost’s public disclosure of three serious vulnerabilities in Go’s encoding/xml related to tokenization round-trips. The public disclosure comes as a result of several months of work, including collaborating with the Go security team since August 2020 and with affected downstream project maintainers since earlier this month.
Securing Your Expanding Network Perimeter
Netreo Platform Security
Now, more than ever, Information Security is a topic that should not be taken lightly. All organizations are vulnerable through technology and it is imperative that risk is managed on a daily basis. Netreo realizes the only way to safeguard against threats is to take a holistic approach to managing our technology, people, and processes.
Using Splunk to Detect Sunburst Backdoor
TL;DR: This blog contains some immediate guidance on using Splunk Core and Splunk Enterprise Security to protect (and detect activity on) your network from the Sunburst Backdoor malware delivered via SolarWinds Orion software. Splunk’s threat research team will release more guidance in the coming week. Also please note that you may see some malicious network activity but it may not mean your network is compromised. As always review carefully.