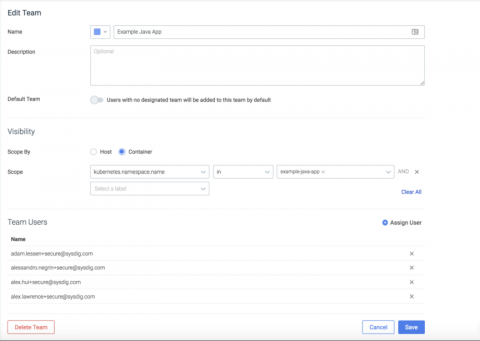
Service based access control with Sysdig Secure Teams
While you’re likely familiar with role-based access control, Sysdig teams introduce the concept of service-based access control. With service-based access control, administrators can define groups of users that have access to policy events, policy configuration, and scanning data limited to a service or set of services, as defined by your orchestration system (think Kubernetes, Mesos, and the like).