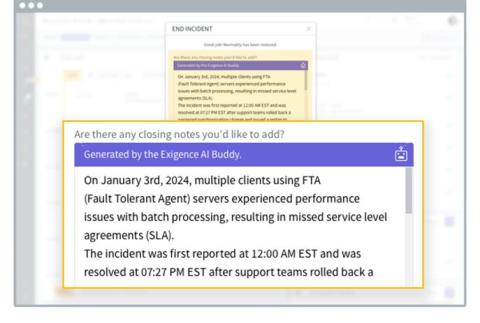
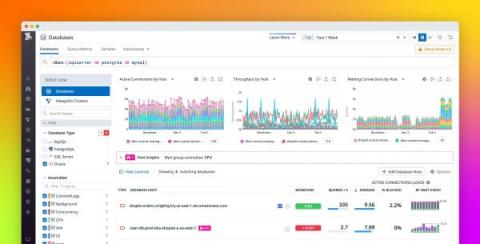
Overcoming Messy Cloud Migrations, Outdated Infrastructures, Syslog, and Other Chaos
As businesses grapple with increasing data volumes, the need for practical tools to manage and use this data has never been greater. High-quality tools are great — but imagine what you could accomplish with one that made all the others in your toolbox even better? That’s exactly how we design every Cribl solution — we exist to help IT and Security teams get more out of their existing infrastructure.