BigPanda and ServiceNow improve IT service management
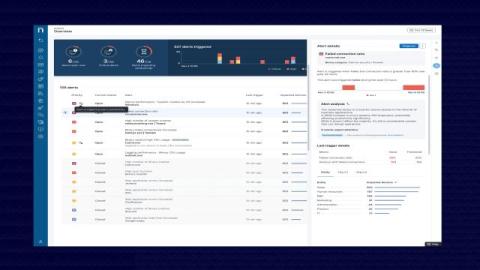
By breaking down the silos between observability, IT operations, and service management, teams can improve service delivery and enhance IT incident management. However, this is more easily said than done. The average BigPanda customer uses more than 20 observability and monitoring data sources. Combining mountains of alert data with legacy event management systems can make it almost impossible to sift through the noise to find the most important alerts.