GitHub Plugin 2.0 release
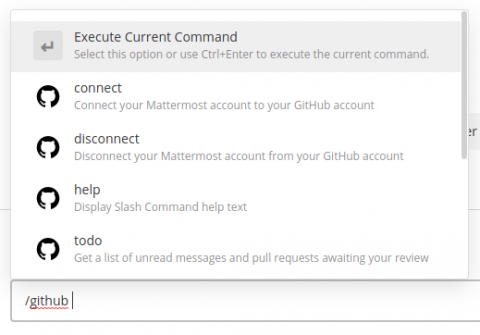
We’re excited to announce the release of GitHub Plugin version 2.0, which adds some new features that increase productivity and reduce the need to context switch between Mattermost and GitHub. As usual, our open source community members have played a key role in developing all of these features and I’d like to say “Thank You!” for their help. Our GitHub plugin is one of the most popular integrations on Mattermost and we use it every day as part of our development process.