Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Modern App Reliability with Sumo Logic Observability
The Internet of Things - Why Cloudsmith Plays a Crucial Role
IoT is slowly, quietly taking over the world. A few years ago, self-ordering fridges, driverless cars, and fully automated homes seemed like the stuff of dreams. And while the technology exists, rollout and adoption is slower than anticipated, amidst security and privacy concerns. That said, IoT is the future, and growth is steady, as the challenges of building and maintaining hundreds of thousands of devices per vendor are getting solved.
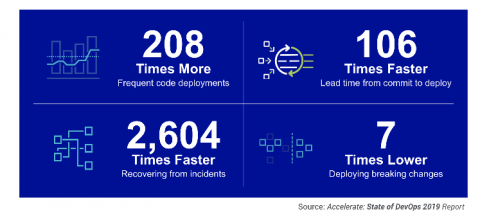
Building competitive advantage by adopting cloud-native approach
With the economies of many countries heading towards recession, increasing regulations, growing security threats and increasing costs, financial services firms need practical solutions, now more than ever. Many of the financial technology firms (‘fintechs’) and mobile app-based challenger banks have taken advantage of modern application architectures and DevOps practices that are associated with cloud native technologies.
Using Social Media for Affiliate Marketing
Today, social media uses a wide range of different social networking platforms to help its users with the creation and sharing of ideas, information, personal interests and hobbies by establishing virtual networks. Affiliates can benefit from these groups that use web-based applications to communicate, interact and connect. Affiliates participate by generating content, for example with comments, articles, photos, videos.
11 Useful Project Management Tools for Web Development
Web designers are putting their time, effort, and creativity into creating a site that appeals to users, and engages, and holds their attention. According to one episode of the Project Management Podcast, it’ll be easier for designers to turn those ideas and concepts into a tangible web design using the right tools. But with so many tools out there in the market, picking the right one can be difficult. So, what will a designer do?
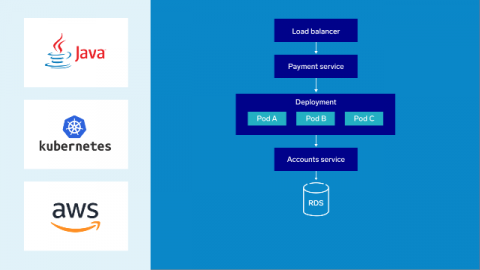
A Quick Guide on How to Lower OpEx through Containerization of Legacy Apps
If you want to put yourself ahead of your competition, you must improve and lower operating costs as much as possible. And, as business owners, you should always be on the lookout for ways to reduce the operating costs without sacrificing the quality of your offering. The same is true with legacy apps! I guess it’s on the higher side for legacy apps because they are not only outdated but can also hamper innovation at all fronts.
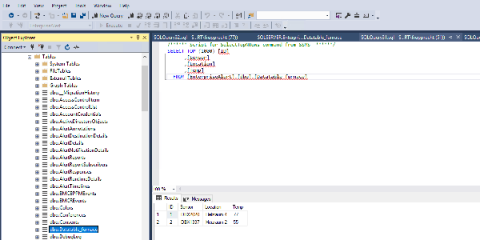
Alerts out of your database (SQL, Powershell, REST API)
Whether it be on the administrative side of the house or in a production environment, the digital world is not slowing down. In fact, it is increasing by the second. Data is collected from a thousand different sources and often stored in the same number of places. Automating the collection, analyzing and augmentation of this data can be quite a cumbersome task and very time-consuming. Not to mention the loss in revenue when this is not done.
ServiceNow global survey shows how COVID-19 is changing work
Today ServiceNow released The Work Survey, a comprehensive global view on how COVID-19 is changing work and the opportunities ahead for a wave of digital innovation in how people work and businesses operate. Executives and employees surveyed in 11 countries across multiple industries agree: technology enabled them to pivot to new ways working faster than thought possible, and digital transformation will accelerate innovation.
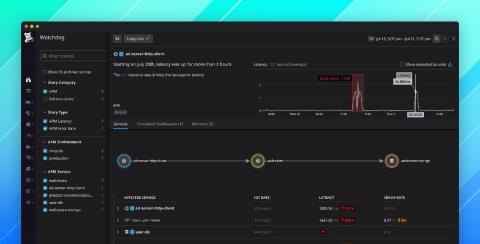
Watchdog surfaces root cause insights and Kubernetes anomalies
Since 2018, Watchdog has provided automatic anomaly detection to notify you of performance issues in your applications. Earlier this year, we introduced Watchdog for Infra, enhancing Watchdog to also monitor your infrastructure. We’re pleased to announce the latest enhancements to Watchdog, which now provides more visibility and greater context around the full scope of each application issue.