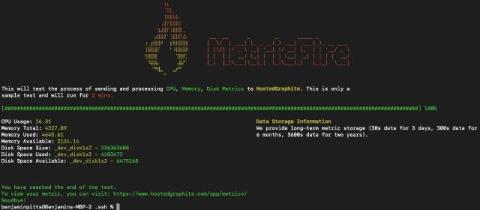
New Onboarding CLI!
We are so excited to share our latest feature with you… our onboarding CLI demo tool! This tool lets new users see how our platform works quickly and seamlessly. You can transfer real CPU, DISK, and RAM data from your device to your account in under five minutes.