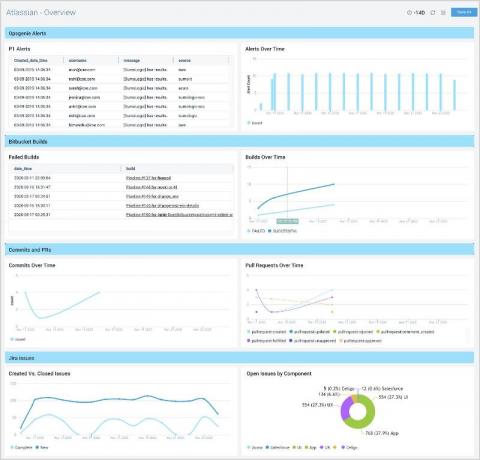
VLAN, WLAN, LAN... and other types of networks you should know
If you thought the fishmonger’s hair net was the only kind of net you’re wrong. From Pandora FMS we will show you some more, so that you do not get lost without them. The term “network” is used in computing to name a set of computers connected to each other in such a way that they can share resources, services, and information. There are several ways to classify these networks, based on their scope, relationship, or connection method.