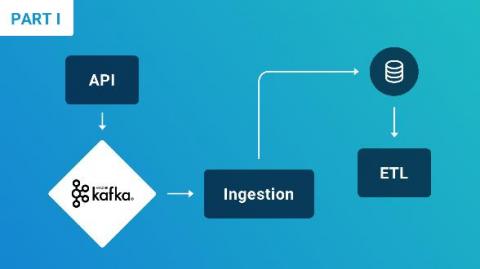
How to promote a status page to your customers?
You set up a status page. Your colleagues have already subscribed to it and are getting all the required notifications. Now internally everybody is aware of the status page service. But now there is the next challenge - make people outside of the company aware of it and use it.