Operations | Monitoring | ITSM | DevOps | Cloud
DevOps
The latest News and Information on DevOps, CI/CD, Automation and related technologies.
Bolstering Our Commitment to Security With SOC 2
September 2019 Online Meetup: Implementing Infrastructure as Code
Datadog + New Relic: Monitor every layer of your stack
Application performance monitoring (APM) dovetails nicely with infrastructure monitoring, allowing you to monitor app performance and end-user satisfaction in context with the rest of your infrastructure. That’s why we unveiled Datadog APM to complement our infrastructure monitoring platform and provide full-stack observability.
Efficiently retrieve old logs with Datadog's Log Rehydration
Logs provide invaluable information about issues you need to troubleshoot. In some circumstances, that may mean that you have to look back at old logs. For example, you may be running a security audit and need to analyze months-old HTTP request logs for a list of specific IP addresses over a period of time. Or you might need to investigate why a scheduled service never occurred, or run an exhaustive postmortem on incidents that happened over a couple months but that you suspect are related.
Deep in the heart of Tech-sys: SpiceWorld 2019 Recap!
In case you missed it, we just wrapped up our keynote to kick off SpiceWorld 2019! Last year, we shared our vision to empower you to use technology to transform your organizations, community, and the world – every day. This year, you’re seeing the first steps of that vision coming to life!
The 2020 State of IT: Four tech trends to watch
Many say that in the world of tech, the only constant is change. For businesses, this dynamic reality presents opportunities as companies continuously scan the horizon for new IT products and services they can deploy to help them stay competitive. At the same time, businesses must navigate computing challenges, such as staying up to date and safe in an expanding universe of cyberthreats.
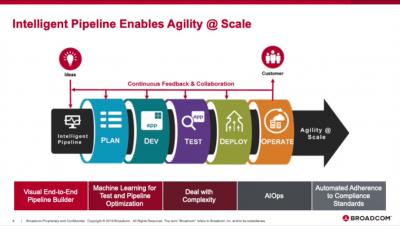
Introduction to intelligent pipeline
Cloudsmith + CircleCI
Cloudsmith provides first-class support for CircleCI with our official orb. Using the orb, users can easily integrate publishing to Cloudsmith with their existing CircleCI workflows.
Chef vs Puppet: Differences, Similarities, and How to Choose
Chef and Puppet are two popular tools for configuration management. These type of tools help engineers to maintain a consistent configuration in all servers. For instance, all servers might need to have IIS with a binding to port 443 for HTTPS access and the respective firewall rule for inbound traffic. More importantly, if anyone removes the firewall rule, these type of tools will keep consistency by creating the firewall rule again.