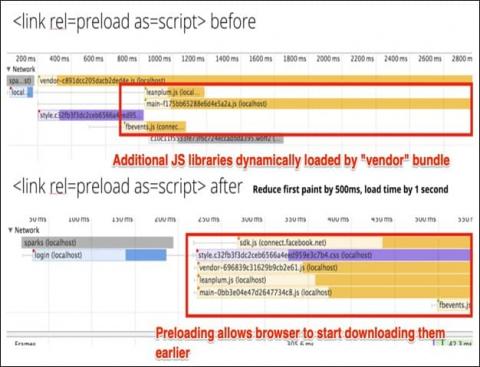
Analyzing Log Data: Why It's Important
From production monitoring to security concerns, businesses need to analyze and review their logs on a daily basis to make sure their system is up to par. Here are the reasons why analyzing your log data is so important. If you landed here, chances are you probably know what logs are, but we’ll start off with a short explanation of what it is.