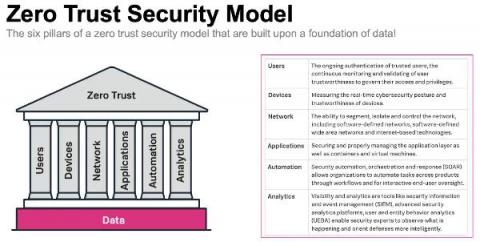
The Evolving World of GitOps and Observability
Is GitOps changing observability as we know it? GitOps has been the buzz word in the DevOps space for several years. GitOps, to those that are not familiar, is an operational methodology for DevOps that leverages a continuous deployment approach with Git as the single source of ‘truth’ for declarative control over both infrastructure and applications.