Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
Multi-cloud trends in the healthcare sector
4 Most Common Website Security Threats (2023) + Solutions
For infrastructure administrators tasked with ensuring the reliable operation of their applications, the thought of a lurking cyberattack can be one to lose sleep over. An attack on your system and the services you provide could render your applications unresponsive, resulting in a security breach, or loss of data.
3 Most Common SD-WAN Issues
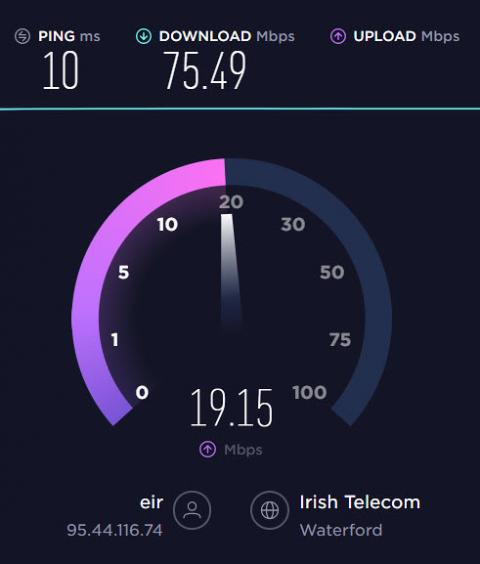
How to monitor Internet quality and ISP performance with Netdata
Find out how to monitor your Internet speed and quality and how well your ISP is performing.
Crous Paris Mitigates Network Outages Before Students Notice with Progress WhatsUp Gold
How to Automate and Orchestrate Your Network Effectively
We explain how to make the most of automation, orchestration, and Infrastructure as Code tools for your highest performing network yet.
How network admins benefit from DNS failover
Downtime is a nightmare, and every network or app administrator wants to avoid it in any way they can. The longer the downtime, the greater the potential for a loss of revenue and a damaged reputation for the organization.
Cybercrime Trends and the Economy
What is Network Flow Monitoring, and Why You Shouldn't Live Without It
Old network salts likely know all about network flows and the value of network flow monitoring. As former News Editor for Network World and Editor in Chief of Network Computing, network flows are part of my old stomping grounds. In fact, I remember when Cisco invented NetFlow in the late 1990’s to collect traffic data from its routers and switches so it could be analyzed by network pros.