Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
Packet Loss Testing and Reducing Guide + Recommended Tools
Understanding Load Balancing Essentials
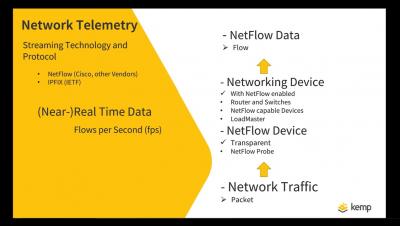
In this post we’ll review some of the essential ideas in Load Balancing to help you understand how to get the best configuration for your application. Load balancing is an essential part of any application deployment to provide high availability, performance and security. We’ll focus on understanding and selecting scheduling and persistence algorithms and using the new LoadMaster Network Telemetry feature to validate the results.
Turn your home office into a NOC room with Philips Hue and Grafana
I recently got a couple of Philips Hue Play lights to spice up my home office setup, and after a bit of tinkering with the APIs, I decided it would be a fun project to create my own personal NOC room, using them to visualize the status of some system I’m monitoring.
The What and The Why of TLS Inspection
Building a complete network security checklist
Understanding what to audit in a network can be chaotic and confusing. Building a complete network security checklist is crucial for organizations with computers connected to the internet or to each other. Think of it like an antivirus scan you might run on your computer to find Trojans or malware, except you’re scanning your entire network to find anything that may cripple it.
Kemp Flowmon Packet Investigator 11.1 - A new user experience
The Kemp Flowmon Packet Investigator 11.1 is easier to use and covers a broader scope of root-cause analysis scenarios.
Understanding The Move To Intelligent Networking
Visualize HAProxy Metrics with InfluxDB
HAProxy generates over a hundred metrics to give you a nearly real-time view of the state of your load balancers and the services they proxy, but to get the most from this data, you need a way to visualize it. InfluxData’s InfluxDB suite of applications takes the many discrete data points that make up HAProxy metrics and turns them into time-series data, which is then collected and graphed, giving you insight into the workings of your systems and services.