Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Event Log Management and Monitoring
Computer networks all around the world generate daily records of events occurring in their system. Some events are routine while others indicate potential security breaches or weak network health. Event log files consist of log information that can help organizations reduce their exposure against malware, intruders, damages and legal obligations.
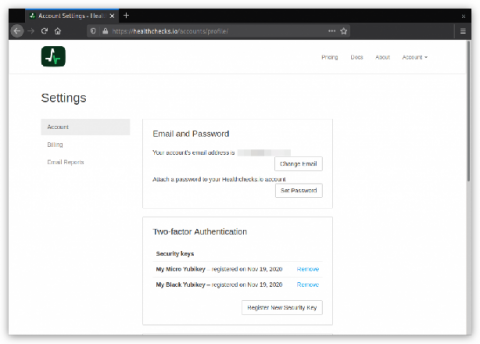
Two-factor Authentication
Healthchecks.io now supports two-factor authentication using the WebAuthn standard. Here is how it works: in the Account Settings page, users can see their registered FIDO2 security keys and register new ones.
5 Remote Working Best Practices and Tips in the Era of Coronavirus Pandemics
As the COVID-19 pandemic sweeps the world, the need has arisen for workers everywhere to adopt remote working practices wherever possible. Remote working presents many opportunities for both businesses and individuals to make better use of their time and enjoy a more streamlined approach to task delegation. Through the use of specialized software, such goals can be achieved without demanding more of individual team members or managers.
5 Steps to Financial Services App Modernization
In recent years, traditional financial services companies have increasingly come under attack from fast-moving financial technology firms—or “fintechs”—which use software to erode the market share of their competition.
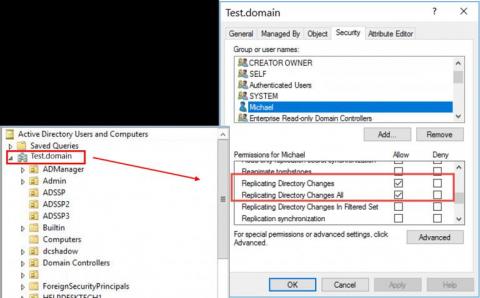
IT security under attack blog series: Instant domain persistence by registering a rogue domain controller
In this blog in the IT security under attack series, we will learn about an advanced Active Directory (AD) domain controller (DC) attack to obtain persistence in AD environments. Dubbed DCShadow, this is a late-stage kill chain attack that allows a threat actor with admin (domain or enterprise admin) credentials to leverage the replication mechanism in AD to register a rogue domain controller in order to inject backdoor changes to an AD domain.
PCI Logging Rules Your Organization NEEDS to Know
For an organization to be compliant with PCI logging requirements, it must follow PCI Requirement 10 of the Payment Card Industry Data Security Standards (PCI DSS). Below, we’ve listed the highlights of this section and the important details that you need to know.
What's new in Sysdig - November 2020
Welcome to another monthly update on what’s new from Sysdig. Our team continues to work hard to bring great new features to all of our customers, automatically and for free! Outside of building awesome new features and functions this month, we also had a lot of fun running cards against containers for a cause once again. If you missed it, feel free to catch-up on YouTube!
Secure your infrastructure in real time with Datadog Runtime Security
From containerized workloads to microservice architectures, developers are rapidly adopting new technology that allows organizations to scale their products at unprecedented rates. In order to make sense of these complex deployments, many teams are abstracting applications away from the environments in which they run. Because of this trade-off, developers and security teams lose the access to the unified context from infrastructure to application needed to fully secure their services.
Zoom into Kinsing
The Kinsing attack has recently been reported by security researchers, and it is well known for targeting misconfigured cloud native environments. It is also known for its comprehensive attack patterns, as well as defense evasion schemes. A misconfigured host or cluster could be exploited to run any container desired by the attacker. That would cause outages on your service or be used to perform lateral movement to other services, compromising your data.