Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Calico Enterprise 3.0 with Calico Multi-Cluster Management
As our enterprise customers build out large, multi-cluster Kubernetes environments, they are encountering an entirely new set of security challenges, requiring solutions that operate at scale and can be deployed both on-premises and across multiple clouds.
How to Choose Incident Alert Management Tools for Your SOC
A security operations center (SOC) is the centralization of your security processes and tooling. It can enable you to monitor for, evaluate, and respond to incidents across your organization with increased efficiency and effectiveness. By centralizing your security efforts, you create greater visibility into your systems and can better analyze and detect threats. At the core of an SOC is your SOC team.
Enforcing CIS compliance with Puppet
Passing an audit is hard — whether you’re in retail, healthcare, finance, or honestly, any industry that values security. Most organizations these days are faced with regulatory standards that must be enforced, which bring both technical and business challenges that are difficult to overcome.
How important is network compliance for your remote work environment?
With a majority of the workforce now adopting a work-from-home routine, maintaining the normal functioning of your network and ensuring compliance with industry standards is not an easy job. When employees are working remotely, it is especially crucial to ensure network compliance with industry standards and internal policies to secure your network from cybersecurity breaches.
How implementing a BYOD initiative helps prepare remote workers for COVID-19 era challenges
As the COVID-19 pandemic continues to force employees to work from home, businesses are facing new and unique challenges to ensure business continuity. When remote work is mandated due to COVID-19, the transition isn’t smooth for many businesses; not every business has the infrastructure to make the abrupt shift, even given the immediate need to go remote.
Email, security, and breaches
Email-based attacks can take many forms, and are typically deployed by cybercriminals in order to extort ransom or leak sensitive data. Just recently, a banking Trojan named Trickbot targeted Italy, a hotspot for COVID-19 cases, with email spam campaigns. While the email subject line is in line with the daily concerns and talks about spread of the virus, the attachment was actually a malicious script.
Profiling "VIP Accounts" Part 1
Cybersecurity use cases for better remote workforce management
In the new normal, if your business has chosen remote operations, this might attract malicious actors. Hackers prey on the remote workforce whose vulnerability has increased in multifold ways. While infrastructural concerns, such as working outside the corporate IT network and using home Wi-Fi are inevitable, other issues, including using personal devices and retaining privileges to access more than required business resources add to the magnitude of this vulnerability.
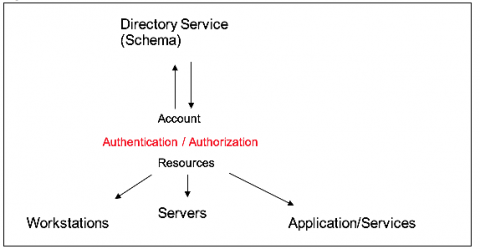
How Identity Management Authentication Works
An organization can have multiple systems like Active Directory, SharePoint, Oracle, Outlook, Teams or simply web applications and they may have hundreds or thousands of employees or outside organization users that can access these systems. Managing accounts of every user and allowing proper access to their respective system is called Identity and Access Management (IAM).