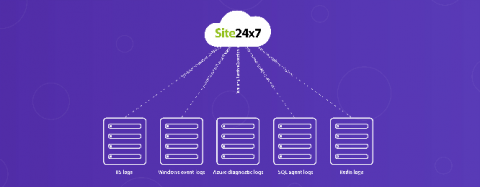
Log management: The key to centralized log aggregation and easy troubleshooting
A large number of security breaches are impacting industry verticals, including banking, financial services and insurance (BFSI), telecom, and hospitality, so there's a growing need for organizations to fortify their infrastructure against these threats. For example, by the time T-Mobile identified the intrusion and unauthorized access to its sensitive data in 2019, both its customer and employee details were already stolen by hackers.