Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
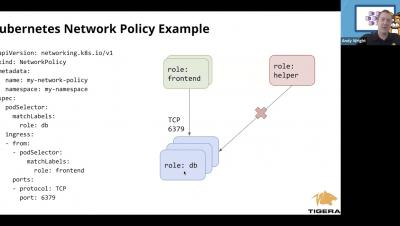
How to Implement Network Policy in Amazon EKS to Secure Your Cluster
Security configurations-Part one: 7 reasons why security configurations are crucial to your security blueprint
Security configurations are security-specific settings used to secure heterogeneous endpoints such as servers, desktops, laptops, mobile devices, and tablets. As endpoints in your network diversify, securing each endpoint becomes a challenge. One way to ensure effective endpoint security is by automating it, which is where security configurations come into play. Security configurations are utilized to secure and control every facet of your network.
Master Class - PCI Compliance and Vulnerability Management for Kubernetes - 2020-05-05
How to Implement Network Policy in Azure AKS to Secure Your Cluster
What is Your Data Worth in the Fight Against Fraud?
You don’t need us to tell you that fraud and financial crime is on the rise. A quick google search will give you endless stats to support this claim. Fraud losses are increasing as a percentage of revenue, and that direct impact on the bottom line isan area of laser focus for senior execs.
Virtual Meetup: SIEM 101: What, Why & How of Information Security
Secure DevOps at the Edge with Sysdig and IBM
Innovative companies are looking to take advantage of cloud-native technologies beyond the data center to deliver faster innovation and competitive advantage at the edge. Recognizing the need for a common approach to create, deploy, run, secure, monitor, maintain and scale business logic and analytics applications wherever your business takes you, IBM today announced its edge computing offerings, including the IBM Edge Application Manager.
Securing Kubernetes with Open Source Falco and Logz.io Cloud SIEM
In a previous blog post I discussed the complexity of securing Kubernetes environments, and some best practices. Unfortunately, even if we follow best practices in setting up and configuring our system, we can never eliminate all the vulnerabilities.
Securely execute a BYOD policy for your remote employees
From global pioneers to budding startups, almost every organization around the globe has adopted a mandatory work-from-home routine due to the COVID-19 outbreak. This shift has brought up numerous questions for decision-makers: How are we going to pull this off? Is work-from-home strategy feasible? Is our network security going to be compromised? Is BYOD the solution?