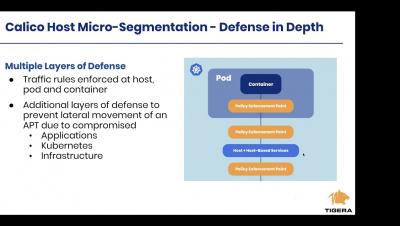
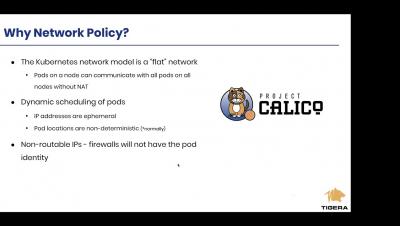
Splunk Attack Range Now With Caldera and Kali Linux
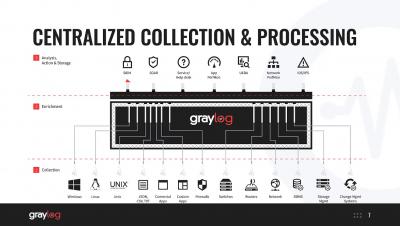
The Splunk Security Research Team has been working on new improvements and additions to the Splunk Attack Range, a tool that allows security researchers and analysts to quickly deploy environments locally and in the cloud in order to replicate attacks based on attack simulation engines. This deployment attempts to replicate environments at scale, including Windows, workstation/server, domain controller, Kali Linux, Splunk server and Splunk Phantom server.