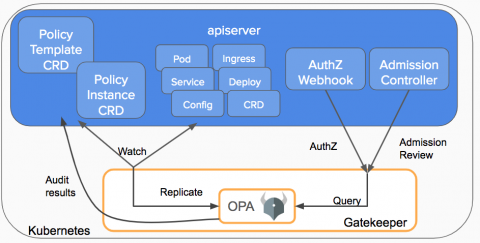
Protecting Your Assets: It's Not Just About Servers and Laptops!
In most of our blogs, we spend a TON of time going on about protecting our endpoints, looking at sysmon, checking the firewall, correlating IDS data and the like… Today, we're going to shift gears a bit and look at security from a different angle. Recently, there has been a tremendous focus on the shifting paradigm of a workforce that primarily resides in corporate offices, to a highly virtual workforce sitting at their kitchen tables.