Enhancing Support for Zeek (Bro) in Logz.io Security Analytics
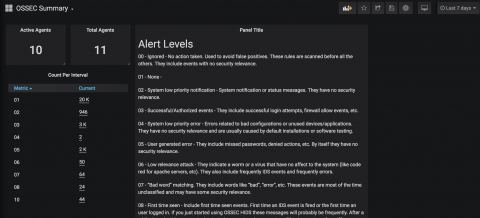
We’re happy to announce official support for Zeek in Logz.io Security Analytics for easier security monitoring! Logz.io Security Analytics provides a unified platform for security and operations designed for cloud and DevOps environments. It’s built on top of Logz.io’s enterprise-grade ELK Stack and is extremely easy to set up and integrate with.