Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
What is observability? Discerning myths from facts
Microservices and distributed architectures have become the norm for building modern day applications. While the cloud has made it easier to deploy and scale microservices, it has opened up a complex set of problems for DevOps by virtue of the sheer volume of interactions between those services.
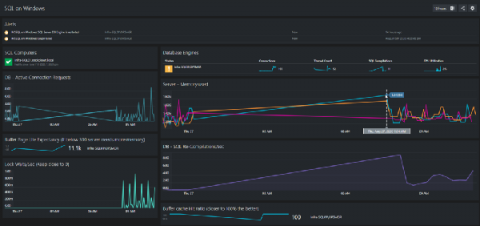
How to maximize the value of SCOM - Monitoring, Alerts, Incidents & Visualization
In SCOM you can see the monitoring that generates your alerts (the contents of Health Explorer). While SCOM doesn’t always make it easy to get at the valuable context that this monitoring data provides, it is there and can help answer the "why" questions that often come up when looking at an alert in isolation.
Node.js Resiliency Concepts: Recovery and Self-Healing
In an ideal world where we reached 100% test coverage, our error handling was flawless, and all our failures were handled gracefully — in a world where all our systems reached perfection, we wouldn’t be having this discussion. Yet, here we are. Earth, 2020. By the time you read this sentence, somebody’s server failed in production. A moment of silence for the processes we lost.
Java Logging: Best Practices for Success with your Java Application
Java is used by at least 7.6 Million developers worldwide. Java logging has been a staple of the Java platform since day one, boasting extensive, resourceful documentation and rich API’s. The cornerstone of monitoring your application is efficient and widespread logging. At Coralogix, we know that logs have become one of the most important components of a modern monitoring function.
All the non-technical advantages of Loki: reduce costs, streamline operations, build better teams
Hi, I’m Owen, one of the Loki maintainers, and I’m putting proverbial pen to paper to convince you why Loki is important. And this isn’t because it scales (it does) or because I work at Grafana Labs (I do). It’s because of the oft-overlooked and underrepresented organizational benefits. Organizational benefits?! What is this, some sort of cult? Why are you avoiding the technicals? Whoa, whoa, whoa. Now, hold on. The technicals are still valid.
The Great Irony of Serverless Computing
Working with Serverless computing is like riding an electric bike. You get speed, flexibility, automatic assistance to scale with ease. Development is usually hassle-free because you can focus on code and only pay for usage of the service. Except when your users hit an error. Debugging that issue feels like your bike’s battery just died while climbing a steep hill.
Secure Your Endpoints with ESET and Logz.io
Watching too many movies might give you the impression that cyber attacks are launched by well-funded masterminds able to control the internet at their whim. But really, successful attacks can be as simple as disguising some malicious software as a link to an often-used site, and tricking people into clicking it, known as phishing. The result is that many cyber attacks are carried out by taking advantage of unsuspecting end users.
Integrate AWS Services into Rancher Workloads with Triggermesh
Many businesses use cloud services on AWS and also run workloads on Kubernetes and Knative. Today, it’s difficult to integrate events from AWS to workloads on a Rancher cluster, preventing you from taking full advantage of your data and applications. To trigger a workload on Rancher when events happen in your AWS service, you need an event source that can consume AWS events and send them to your Rancher workload.
Are you on top of newly introduced errors in your CI/CD releases?
Log files are infamous for being “noisy”. Without the right management solution, trying to find a specific piece of information or using them to reproduce a critical error is a complex undertaking. If you’re working with CI/CD, how do you attribute new errors to a particular release? How do you investigate those errors and make sure that your customers aren’t being impacted? Faster releases mean shorter development and testing cycles before new code reaches production.