Operations | Monitoring | ITSM | DevOps | Cloud
Incident Management
The latest News and Information on Incident Management, On-Call, Incident Response and related technologies.
Launched - Zenduty Web v2.0
We constantly update the platform to provide the best-in-class experience to our users. These updates are not something that we feel is right for the client; these updates are based on the user data, behavior, and requests that our users provide. We are always excited to bring new updates and share them with people but this one is special! We bring to you Zenduty Web v2.0!
The Reverse Red Herring
Micro Lesson: Troubleshoot an Incident Using Root Cause Explorer
Micro Lesson: Understanding Root Cause Explorer
The wait is over.... Zenduty Web v2.0 is here!
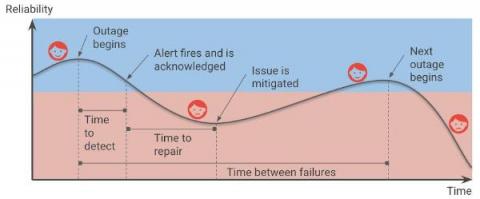
Are your SLOs realistic? How to analyze your risks like an SRE
Setting up Service Level Objectives (SLOs) is one of the foundational tasks of Site Reliability Engineering (SRE) practices, giving the SRE team a target against which to evaluate whether or not a service is running reliably enough. The inverse of your SLO is your error budget — how much unreliability you are willing to tolerate.
How to implement a Blameless Postmortem (part two)
This is Part 2 of a two-part series on Blameless Postmortems. The previous article went into why blameless postmortems are so effective; this second part goes into detail on how to build your own postmortem process and kick it into overdrive. Read Part 1 here. So you've read our first installment and recognized the value of the blameless postmortem for efficiency, culture, and output. Now you're ready to get off the blame train and kickstart a blameless postmortem process of your own. Where to begin?
May 2022 Update - Templates, scheduler enhancements, landline numbers, and more
Our May update brings Signl templates for manual alerting, improvements for duty scheduling and various enhancements in the web portal. Another new feature is the possibility to notify through calling landline numbers. All details can be found in this blog article.
SIEM: Introduction to SIEM and 4 Top SIEM Tools
Security Information and Event Management (SIEM) technology has become a fundamental part of identifying and guarding against cyber attacks. It is one of the essential technologies powering the modern security operations center (SOC). SIEM is an umbrella term that includes multiple technologies, including log management, security log aggregation, event management, event correlation, behavioral analytics, and security automation.