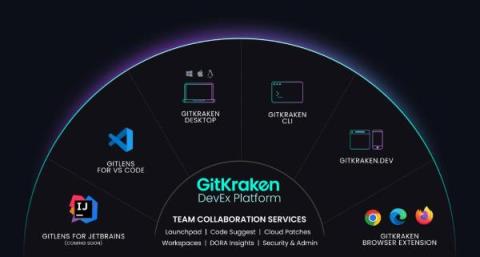
Why we've open sourced our secure SDLC process template
One of the big things we’ve learned since starting Kosli is that engineers often struggle to define an SDLC for compliance purposes. That doesn’t mean they don’t know how to deliver secure, quality software. They’ve just never had to actually define a process for how they do it. Perfectly capable engineers can spend years shipping great products and features without ever having to properly define and standardize their SDLC.