Operations | Monitoring | ITSM | DevOps | Cloud
Monitoring
The latest News and Information on Monitoring for Websites, Applications, APIs, Infrastructure, and other technologies.
Are You Driving Your Rolls Royce Like a Kia?
High performance automobiles are built to be driven on the open road, at high speeds, hugging each curve and accelerating on the straightaways—they’re not for trips to the grocery store.
Basic SQL Server Query Tuning Secrets Every SQL Admin Should Know
The Syslog Staying Power
Deployment Choices for eG Enterprise
You have two choices when deploying eG Enterprise: Wherever you choose to locate your eG Manager, eG Enterprise does not and will never collect data from your systems. There is never a data feed going from eG Manager to any outside system unless specifically configured by the customer and we do not incorporate any dubious call-home technologies. Before installing eG Enterprise, you will also need to consider the factors discussed in the Where to locate the eG Manager?
What Is Network Traffic Analysis? A Helpful Walkthrough
Network traffic analysis is the method of collecting, storing, and analyzing traffic across your network. Traffic data is collected in or near real time so you can have up-to-the-second information about what’s happening. This allows you to take action immediately if a problem arises. You can also store this data for historical analysis.
What Is Network Traffic and How Do You Monitor It?
“Network traffic” is a term that describes the influx and outflux of network packets within an organization’s network. Understanding and monitoring this traffic is an important step in protecting an organization’s health. This blog post discusses what network traffic is, the different types, and how you can monitor it.
An Introduction to Anomaly Detection
In early 1900, Sakashi Toyoda invented a loom that automatically stops when the thread breaks, limiting the need for someone to watch the machine constantly. This approach was later named “Jidoka” and became one of the two pillars of the TPS (Toyota Production System) with just-in-time production representing the second pillar.
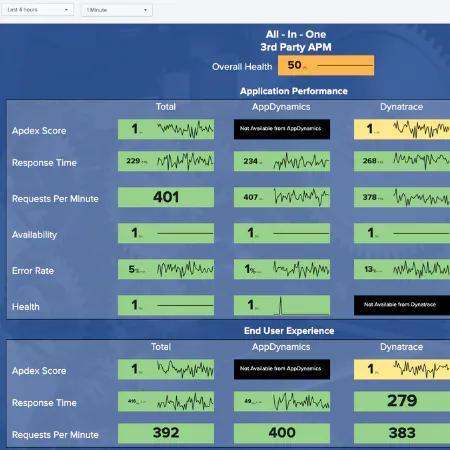
The Best Things Come in Content Packs: Synthetic Managing and Third-Party APM
We recently announced the new Splunk App for Content Packs, your single source for all the goodness that is content packs. This new app makes it easier than ever to get started with Splunk for IT use cases. Individual content packs come with prepackaged content and out-of-the-box searches and dashboards, helping streamline workflows and ensuring you get the most out of your usage with Splunk IT Service Intelligence (ITSI) and Splunk IT Essentials Work (ITE Work).
Best practices for collecting and managing serverless logs with Datadog
Logs are an essential part of an effective monitoring strategy, as they provide granular information about activity that occurs anywhere in your system. In serverless environments, however, you have no access to the infrastructure that supports your applications, so you must rely entirely on logs from individual AWS services when troubleshooting performance issues.