Introducing: Business Impact Alerts
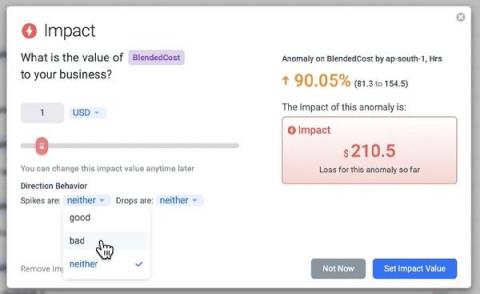
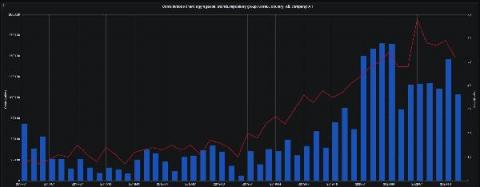
Anodot is the only monitoring solution built from the ground up to find and fix key business incidents, as they’re happening. As opposed to most monitoring solutions, which focus on machine and system data to track performance, Anodot also monitors the more volatile and less predictable business metrics that directly impact your company’s bottom line. Now there’s an easy way to measure the business impact of every incident.